Theory
What is Active Directory
Active Directory (AD) is a directory service developed by Microsoft for Windows domain networks. It is included in most Windows Server operating systems as a set of processes and services. Active Directory plays a crucial role in managing the identities and relationships that make up network environments.
Key Concepts of Active Directory
Domain: The basic unit of structure in an Active Directory network. A domain is a collection of objects such as users, groups, and computers that are managed centrally.
Forest: A collection of one or more domain trees. Forests enable global policies and trust relationships across multiple domains.
Tree: A hierarchy of domains in Active Directory that share a contiguous namespace.
Organizational Unit (OU): A container within a domain that can hold users, groups, computers, and other OUs. OUs allow the organization of objects within a domain and the application of policies at a granular level.
Global Catalog: A distributed data repository that contains a searchable, partial representation of every object in every domain within a forest. It is used to improve query performance and facilitate logon processes across domains.
After Windows system became part of the domain, it's interaction with SAM is over, they've broke up and it's new boyfriend is Domain Controller. And all questions about checking password would now be sent to Domain Controller, not SAM. But in some ways system could come over to SAM if specify the hostname of the device proceeded by the username like WS01/nameofuser.
STRUCTURE EXAMPLE
FIA.LOCAL/
├── FIELD-AGENTS.INLANEFREIGHT.LOCAL
│ ├── GPOs
│ └── OU
│ └── EMPLOYEES
│ ├── COMPUTERS
│ │ └── PC01
│ ├── GROUPS
│ │ └── SQUAD01
│ └── AGENTS
│ ├── solomon.reed
│ ├── alex.xenakis
│ └── song.so.mi
├── CORP.INLANEFREIGHT.LOCAL
└── EXEC.INLANEFREIGHT.LOCAL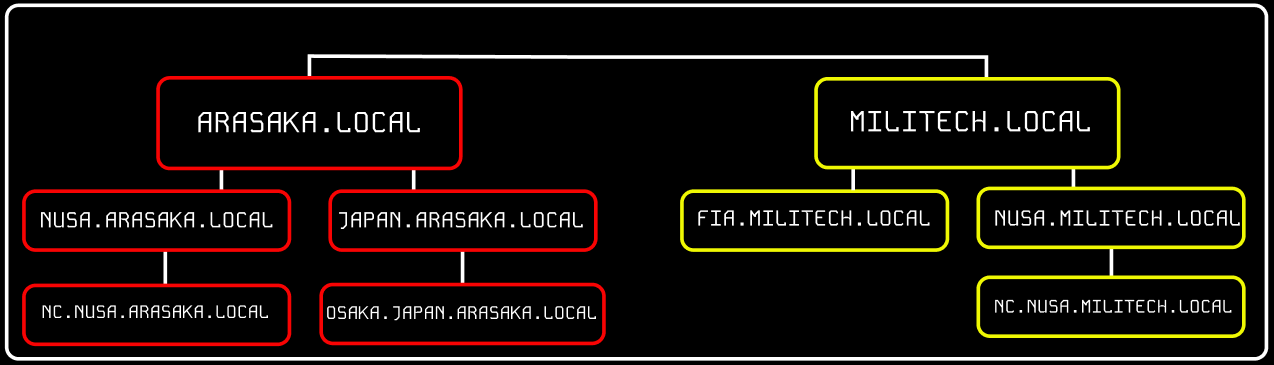
Here we could see domain structure of ARASAKA.LOCAL and MILITECH.LOCAL. Let's imagine that ARASAKA and MILITECH have bidirectional trust between these forests, meaning that users from ARASAKA.LOCAL can access MILITECH.LOCAL.
We can also see multiple child domains under each root domain. In this example, we can see that the root domain trusts each of the child domains, but the child domains in ARASAKA.LOCAL do not necessarily have trusts established with the child domains in MILITECH.LOCAL. This means that a user that is part of OSAKA.JAPAN.ARASAKA.LOCAL would NOT be able to authenticate to machines in the NC.NUSA.MILITECH.LOCAL domain by default even though a bidirectional trust exists between the top-level MILITECH.LOCAL and ARASAKA.LOCAL domains.
ADCS
Active Directory Certificate Services (AD CS) is a Windows Server role for issuing and managing public key infrastructure (PKI) certificates used in secure communication and authentication protocols. So basically it is PKI framework functionality implementation in AD and Windows Server.
CA
Certificate Authority (CA) in Active Directory Certificate Services (AD CS) is a trusted entity responsible for issuing, managing, and validating digital certificates in an Active Directory environment. These digital certificates are used to verify identities, secure communications, and enable authentication across the network.
KERBEROS
Kerberos is default domain accounts authentication protocol since Windows 2000. Main difference between other authentication protocols is that Kerberos use tickets, instead of just transmitting passwords all over the network. This image will show you simplified version of Kerberos authentication process, and then I'll explain everything in parts. Also for more detailed explanations I could recommend to watch [THIS] video.
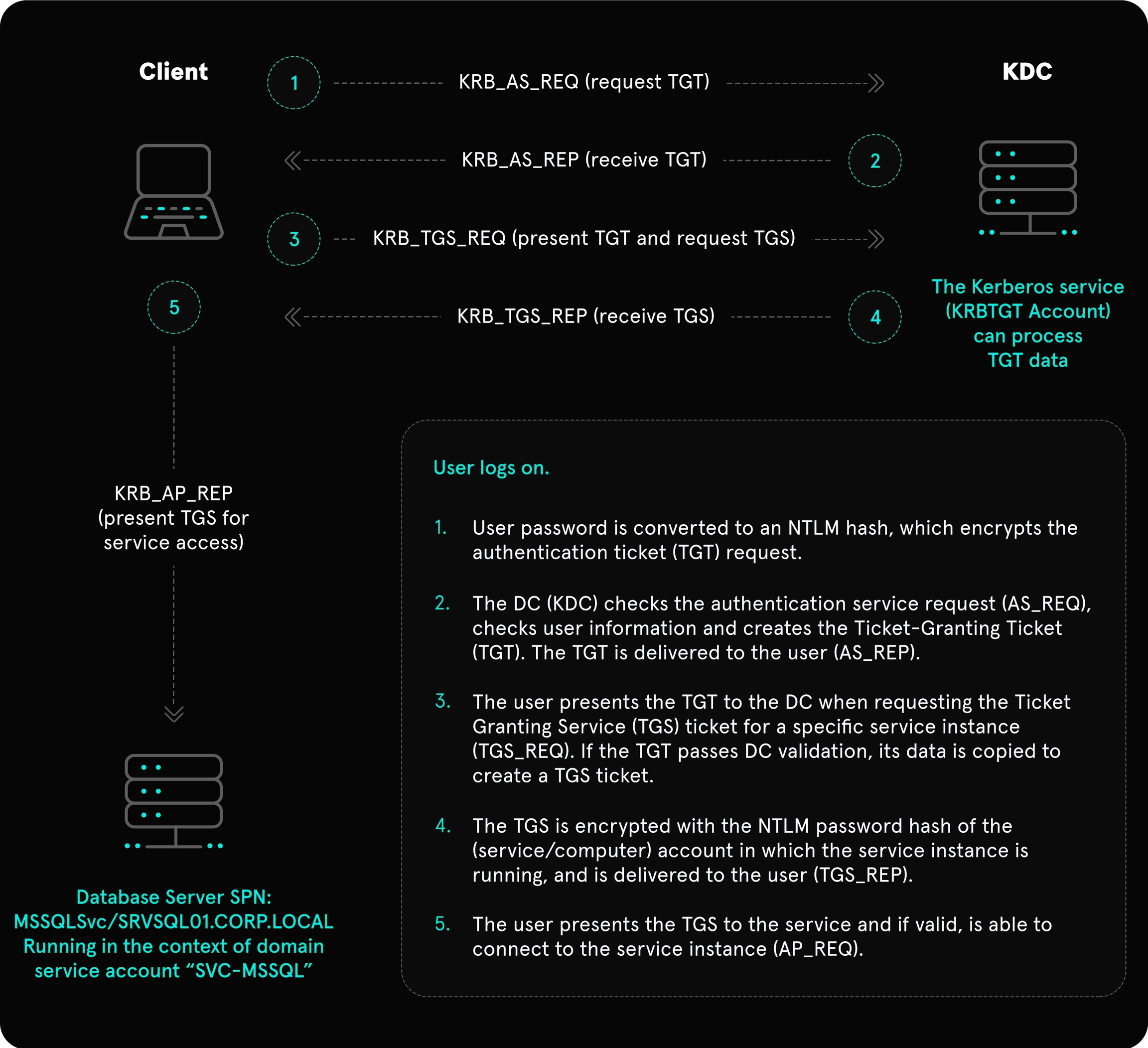
The whole ping-pong of tickets and requests is shows here:
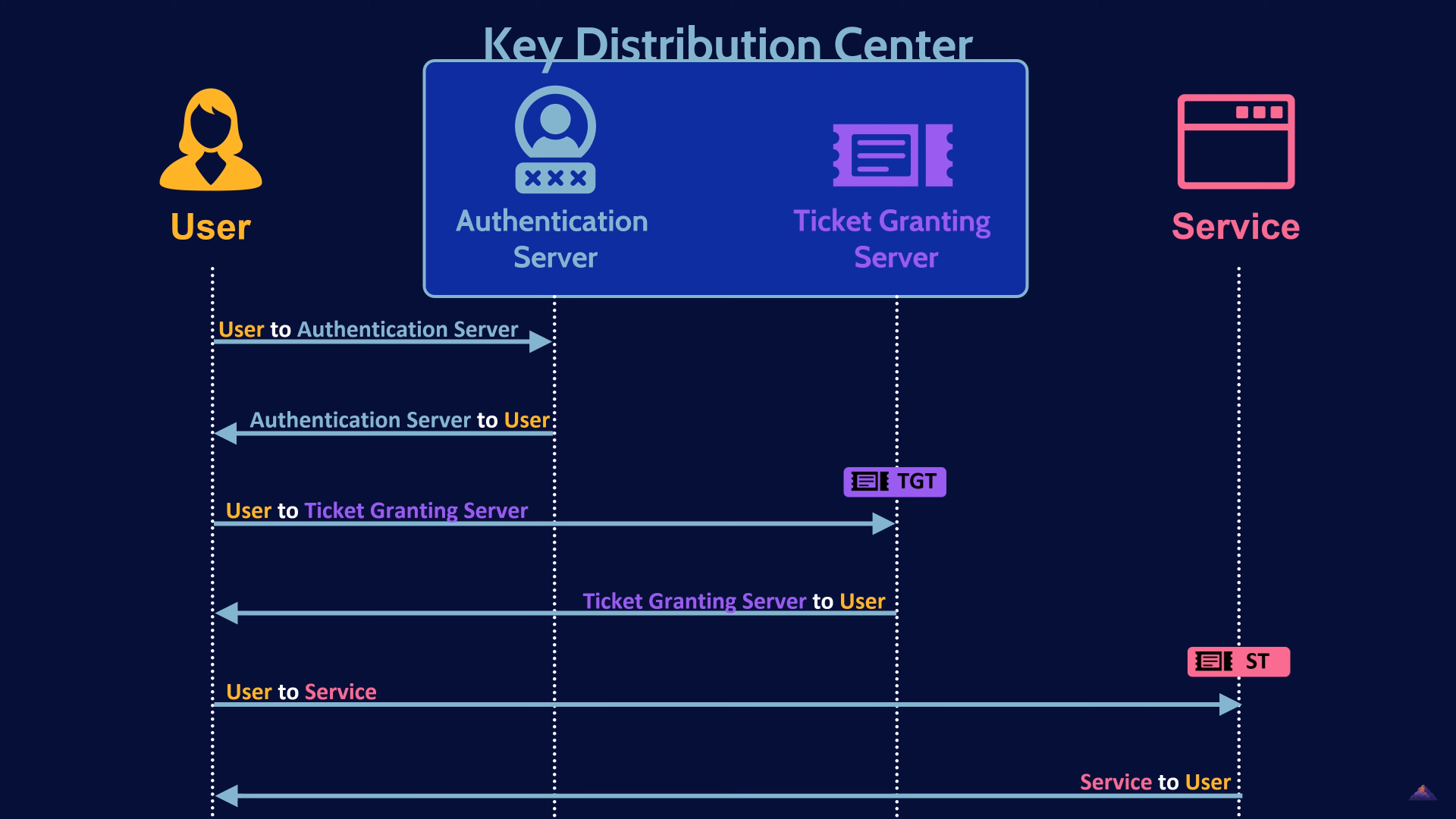
Main Kerberos Terms
Key Distribution Center (KDC):
Core of Kerberos authentication that manages secret keys and distributes them to clients and servers. It is divided into two main components: the Authentication Server (AS) and the Ticket Granting Server (TGS).
Authentication Server (AS):
Part of the KDC that verifies the identity of the client. Upon successful authentication, it issues a Ticket Granting Ticket (TGT) to the client, which can be used to request service tickets from the TGS. There are also database with hashes of user credentials.
Ticket Granting Server (TGS):
Part of the KDC that issues service tickets to clients that have a valid TGT. These service tickets allow the client to authenticate to various services without needing to re-enter their credentials. There are also database with service secret keys, which is used to encrypt/decrypt service tickets.
Ticket Granting Ticket (TGT):
Ticket given by the AS to a client upon successful authentication. It contains a session key and is used to obtain service tickets from the TGS. The TGT is encrypted with the TGS's secret key.
Service Ticket: This Ticket allows a client to authenticate to a specific service. It contains encrypted information that verifies the client's identity and includes a session key that the client can use to communicate securely with the service.
NTLM
NTLM (NT LAN Manager) is a challenge-response authentication protocol developed by Microsoft for authenticating users and securing communication in Windows environments. It has been largely replaced by Kerberos in modern Active Directory (AD) environments but is still present for backward compatibility.
How it works?
NTLM uses a challenge-response mechanism to authenticate users without transmitting their passwords in plaintext.
User Requests Access
The client (user) tries to authenticate to a server or domain controller.
Challenge from the Server
The server sends a random nonce (challenge) to the client.
Client Responds with a Hash
The client encrypts the challenge using an NTLM hash (derived from the user's password) and sends it back.
Server Verifies
The server compares the response with its expected hash (computed from the stored user credentials).
NTDS.DIT
NTDS.DIT stands for New Technology Directory Services Directory Information Tree. It is main database file within Microsoft’s Active Directory Domain Services (AD DS). NTDS.DIT stores and organizes all the information related to objects in the domain, including users, groups, computers, and more. It acts as the backbone of Active Directory, housing critical data such as user account details, passwords, group memberships, and other object attributes.
LDAP
LDAP (Lightweight Directory Access Protocol) is a protocol used to access and manage directory services over a network. It stores information in a hierarchical structure and is often used for user authentication, authorization, and managing resources like contacts or network devices. LDAP allows operations like searching, adding, modifying, and deleting directory entries. It's commonly used in systems like Microsoft Active Directory for managing user data and permissions.
TRUST
Trust enables authentication between forests or domains, allowing users to access resources or manage another domain outside their own. It establishes a connection between the authentication systems of the two domains.
Trust Type
Description
Parent-child
A trust between domains within the same forest, where the child domain automatically forms a two-way transitive trust with its parent domain.
Cross-link
A direct trust between child domains designed to optimize authentication processes.
External
A non-transitive trust between domains in separate forests that are not connected by a forest trust. This type of trust employs SID filtering.
Tree-root
A two-way transitive trust between the root domain of a forest and a newly created tree root domain. It is automatically established when a new tree root domain is added to a forest.
Forest
A transitive trust between the root domains of two separate forests.
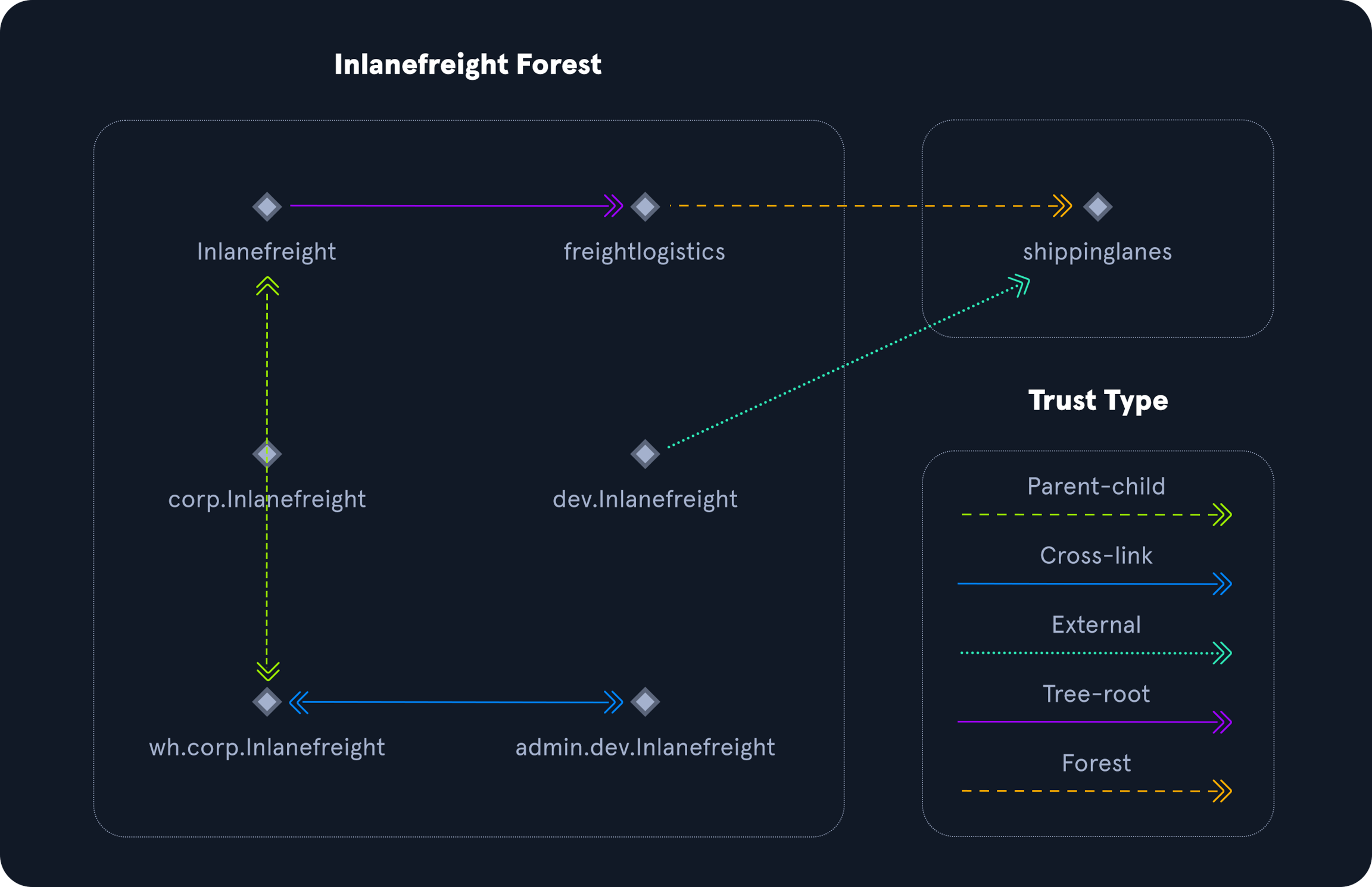
Trusts can be transitive or non-transitive.
A transitive trust means that trust is extended to objects that the child domain trusts.
In a non-transitive trust, only the child domain itself is trusted.
Also they can be one-way, and bidirectional. Here everything is quite obvious, one-way is one way and bidirectional can work in both-ways, back and forward.
GROUPS
In Active Directory (AD), groups are used to manage permissions and assign access to users, computers, and other resources efficiently.
Group Types
Security Groups
Used for assigning permissions to resources (e.g., file shares, printers).
Can be used for Group Policy (GPO) applications.
Example: "IT Admins" security group with admin access.
Distribution Groups
Used for email distribution lists (e.g., Outlook groups).
Cannot be used for permissions.
Example: "HR Team" email group for internal communication.
Group Scopes
Scopes define where the group is used and who can be a member.
Scope
Can Contain
Can Be Used In
Domain Local
Users, groups from any domain
Local domain only
Global
Users, groups from same domain
Any trusted domain
Universal
Users, groups from any domain
Forest-wide
GPO
Group Policy Object (GPO) is a virtual collection of policy settings that can be applied to user(s) or computer(s). Every GPO has a unique name and is assigned a unique identifier (a GUID). They can be linked to a specific OU, domain, or site. A single GPO can be linked to multiple containers, and any container can have multiple GPOs applied to it. They can be applied to individual users, hosts, or groups by being applied directly to an OU. Every GPO contains one or more Group Policy settings that may apply at the local machine level or within the Active Directory context.
Example
Establishing different password policies for service accounts, admin accounts, and standard user accounts using separate GPOs
Preventing the use of removable media devices (such as USB devices)
Enforcing a screensaver with a password
Restricting access to applications that a standard user may not need, such as cmd.exe and PowerShell
Enforcing audit and logging policies
Blocking users from running certain types of programs and scripts
Deploying software across a domain
Blocking users from installing unapproved software
Displaying a logon banner whenever a user logs into a system
Disallowing LM hash usage in the domain
Running scripts when computers start/shutdown or when a user logs in/out of their machine
PKI
PKI (Public Key Infrastructure) is a framework that provides the creation, distribution, management of digital certificates. It ensures secure communication over networks by authenticating users, devices, and services through the use of public and private key pairs.