Theory
OS Structure
In Windows, the root directory is <drive_letter>:\ (usually C:), where the OS is installed. Other drives, like Data (E:), are assigned different letters. The boot partition’s directory structure includes key system folders:
Perflogs
Holds performance logs (empty by default).
Program Files
Contains 64-bit programs on 64-bit systems, 32-bit programs on 32-bit systems.
Program Files (x86)
Stores 32-bit programs on 64-bit systems.
ProgramData
Hidden folder for essential program data shared by all users.
Users
Stores user profiles and includes Public and Default folders.
Default
Template for creating new user profiles.
Public
Shared folder accessible to all users and over the network.
AppData
Hidden per-user folder with Roaming (synced), Local (machine-specific), and LocalLow (low integrity) subfolders.
Windows
Contains core files for the Windows operating system.
System, System32, SysWOW64
Holds essential DLLs for Windows and its API.
WinSxS
Stores copies of all Windows components and updates.
SERVICES
Windows Services are long-running executable applications that run in the background and can be automatically started when the system boots, manually started or stopped, and configured to restart upon failure. They are commonly used for core system functions, server applications, and background tasks. Service statuses can appear as Running, Stopped, or Paused, and they can be set to start manually, automatically, or on a delay at system boot.
List all running services
Get-Service | ? {$_.Status -eq "Running"} | select -First 2 |flPROCESSES
Windows Processes are instances of running programs or applications. Each process contains the program's code, data, and resources required to execute tasks. Processes can run in user mode or kernel mode, and they are managed by the Windows operating system through the Process Manager. Also they either run automatically as part of the Windows operating system or are started by other installed applications.
Built-in Service Accounts
Local System Account
NT AUTHORITY\SYSTEM, is the most powerful built-in account in Windows. It is used by the operating system for critical tasks and services and has more privileges than local administrators.
Local Service Account
NT AUTHORITY\LocalService, is less privileged than the Local System Account and is used to run services with minimal rights, having similar privileges to a standard local user.
Network Service Account
NT AUTHORITY\NetworkService, is used for network services that require authentication and has privileges similar to the Local Service Account, but with the ability to access network resources.
REGISTRY
Windows Registry is a collection of databases of configuration settings for Windows. The Registry is a database of all the settings that the Microsoft Windows operating system, its applications, and hardware device drivers use to maintain their configurations.
The Registry is a hierarchical database. At the top of the hierarchy is your computer. Under that, you’ll find the main branches, known as “hives” Within these hives are Registry keys. Keys can contain sub-keys and Registry values.
The entire system registry is stored in several files on the operating system. You can find these under C:\Windows\System32\Config\.
The user-specific registry hive (HKCU) is stored in the user folder (C:\User\rio\Ntuser.dat).
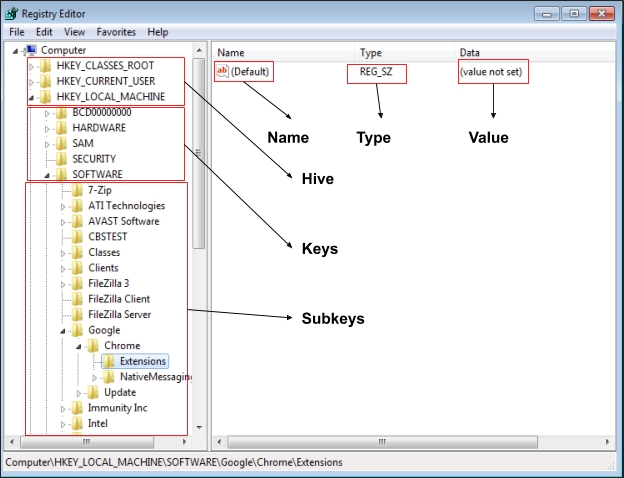
Important Registry Hives
HKEY_CLASSES_ROOT (HKCR)
Information about registered applications, file associations, and OLE (Object Linking and Embedding) objects.
HKEY_CURRENT_USER (HKCU)
Settings specific to the current user, such as desktop settings and application settings.
HKEY_LOCAL_MACHINE (HKLM)
System-wide settings, security policies, and hardware configurations that apply to all users.
HKEY_USERS (HKU)
All user profiles loaded on the computer, including the current user's profile.
HKEY_CURRENT_CONFIG (HKCC)
Information about the current hardware profile of the computer, such as display and printer settings.
Important Registry Keys
HKEY_LOCAL_MACHINE\Security
Security settings, such as account policies and security options.
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
List of programs that run automatically at startup.
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services
Information about system services, including startup type and dependencies.
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings
Internet Explorer settings, such as proxy settings and security zones.
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Windows
Windows configuration information, such as system name and installation path.
ICACLS
ICACLS is a command-line utility in Windows used to display, modify, or back up access control lists (ACLs) for files and directories. ACLs are used to define the permissions and access rights that users or groups have over specific files or folders.
LLMNR & NBT-NS
Link-Local Multicast Name Resolution (LLMNR) and NetBIOS Name Service (NBT-NS) are features in Microsoft Windows that provide alternative methods for host identification when DNS is unavailable. If a device fails to resolve a host through DNS, it will typically attempt to ask other devices on the local network for the correct host address using LLMNR. LLMNR is based on the DNS format and allows devices on the same local network to resolve names for each other. It uses UDP port 5355. If LLMNR doesn't work, NBT-NS takes over. NBT-NS identifies devices on a local network using their NetBIOS names and operates on UDP port 137. The important point is that when LLMNR or NBT-NS is used for name resolution, any device on the network can respond.
DPAPI
Data Protection Application Programming Interface is set of API which Windows uses for the symmetric encryption of asymmetric private keys and used by various third-party applications like:
Internet Explorer
Google Chrome
Outlook
Remote Desktop Connection
Credential Manager
WMI
Windows Management Instrumentation (WMI) is a subsystem of PowerShell that provides system administrators with powerful tools for system monitoring. The purpose of WMI is to unify the management of devices and applications across corporate networks.. WMI allows read and write access to almost all settings on Windows systems. Mostly uses TCP port 135
You can see WMI Command-Line Interface (WMIC) commands for [CMD] and [PowerShell] here.
WMI Usage
WMI can be used for a variety of purposes, including monitoring the status of local or remote systems and configuring security settings on remote machines or applications. It allows for managing user and group permissions, modifying system properties, and executing code. Additionally, WMI supports scheduling processes and setting up logging functionalities.
WMI Components
Component
Description
WMI Service
Runs at boot and acts as an intermediary between providers, repository, and applications.
Managed Objects
Logical or physical components managed by WMI.
WMI Providers
Monitor events and data for specific objects.
Classes
Pass data to the WMI service via providers.
Methods
Enable actions such as starting or stopping processes.
WMI Repository
Stores static WMI data.
CIM Object Manager
Handles data requests and responses.
WMI API
Allows applications to access the WMI infrastructure.
WMI Consumer
Queries objects via the CIM Object Manager.
Tips2Hack
WMIexec.py
Get all service paths
SysInternals
Windows Sysinternals is a powerful suite of utilities created by Mark Russinovich, which is now owned by Microsoft. These tools are primarily designed for system troubleshooting, monitoring, and diagnostics, but they can also be extremely valuable for security researchers and ethical hackers. The tools are used to understand the internal workings of Windows, uncover security weaknesses, and perform forensic analysis. The tools can be either downloaded from the Microsoft website or by loading them directly from an internet-accessible file share by typing \\live.sysinternals.com\tools into a Windows Explorer window.
Examples and command you could see here: [LINK]
Named Pipes
Named Pipes in Windows are a mechanism for inter-process communication (IPC) that allows data exchange between processes, either locally or across a network, using a unique name (e.g., \\.\PipeName\\ExampleNamedPipeServer). They support bidirectional communication, can transfer data securely using Windows access control, and are commonly used for client-server communication or remote management tasks. Cobalt Strike uses Named Pipes for every command (excluding BOF).
Cobalt Strike utilizes Named Pipes for executing commands. The process involves starting a named pipe, injecting a command into a new process, and directing the output to the pipe, ensuring isolation from beacon crashes or antivirus detections.
There are two types of pipes: Named Pipes, which are persistent and have specific names, and Anonymous Pipes, which are temporary and unnamed.
The client-server model governs Named Pipes, where the server creates the pipe, and the client communicates with it. This can operate in half-duplex (one-way) or duplex (two-way) communication modes.
Important Files Location
C:\Windows\System32\drivers\etc- Local DNS file, same role as Linux** /etc/hosts**
Last updated