Theory
Kubernetes
Kubernetes is an orchestration framework for software containers. Kubernetes provides the tools you need to run containerized applications in production and at scale. Google Kubernetes Engine (GKE) is a managed service for Kubernetes.
Cloud Computing
Principles of Cloud Computing:
Customers get computing resources that are on-demand and self-service
Customers get access to those resources over the internet, from anywhere.
The provider of those resources allocates them to users out of that pool
Resources are elastic - which means they're flexible, so customers can be
Customers pay only for what they use, or reserve as they go
GKE Structure
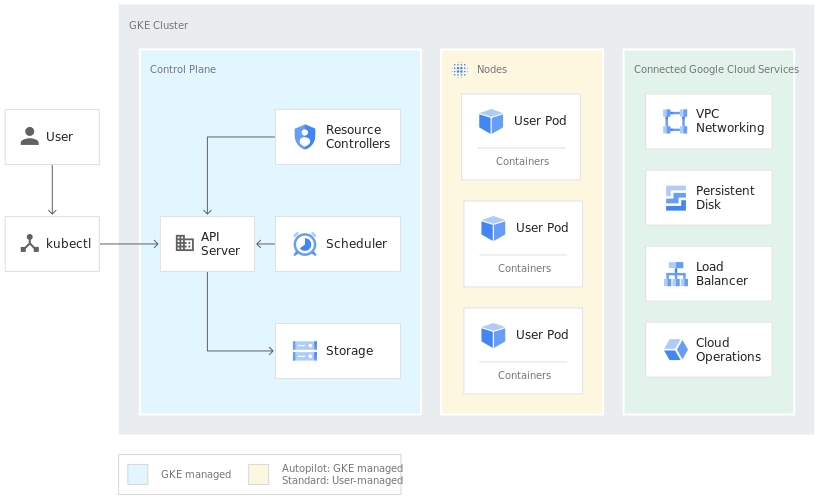
Cluster: A Kubernetes cluster is a set of nodes (machines) that run containerized applications managed by Kubernetes. It includes a control plane and nodes.
Pod: The smallest and simplest Kubernetes object. A pod represents a single instance of a running process in a cluster and can contain one or more containers.
Node: A machine (virtual or physical) in a Kubernetes cluster that runs pods. Nodes are managed by the control plane.
Control Plane: The collection of processes that manage the Kubernetes cluster. This includes the API server, scheduler, controller manager, and etcd database. It is responsible for maintaining the desired state of the cluster.
kubelet: An agent that runs on each node in the cluster. It ensures containers are running in a pod by communicating with the control plane.
kubectl: A command-line tool for interacting with the Kubernetes API server. It allows you to deploy and manage applications on a Kubernetes cluster.
Google Computing Services List
Compute Engine, GKE, App Engine, Cloud Functions, and Cloud Run
Batch Job
In the simplest terms, a batch job is a scheduled program that is assigned to run on a computer without further user interaction. Batch jobs are often queued up during working hours, then executed during the evening or weekend when the computer is idle
Service Accounts
Service accounts are identities that are intended for use by applications instead of people. In GKE, you interact with Kubernetes service accounts and with Identity and Access Management service accounts.
Account Impersonation
GKE Service Account Impersonation allows one Google Cloud service account to act on behalf of another service account. This is useful for granting temporary permissions and enhancing security.