BloodHound
ABOUT
BloodHound is a powerful security tool that uses graph theory to reveal the relationships between users, groups, and computers in a domain [LINK]. Also it have companion tool ShardHound [LINK].
INSTALL
I'm not SpecterOps, but for install guide you can look up here: [LINK]
Then just go it directory tool installed BH (in my situation it's /opt/Bloodhound)
Turn On
docker compose upTurn Off
docker compose stopCheck how much memory BH takes
docker system dfUSAGE
Access
After you composed, just go to http://127.0.0.1:8080/ui/login and use user admin and password which you should find at the first time boot up in output. Then change password ofc.
Collectors
You can't use BloodHound if you don't have Collector's (SharpHound or AzureHound, depends on what you hacking) output - specific programs which collect all data user permissions allow, and pack it in a bunch of json files in zip archive.
You can install the newest version of SharpHound in Download Collectors field.
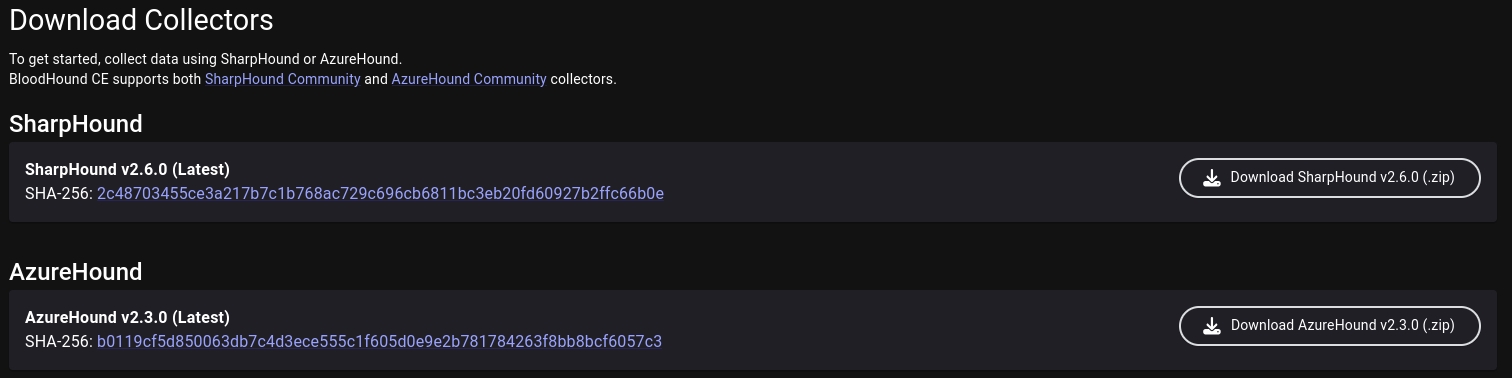
Then after you have SharpHound on your system, you should place it in targets system. How you would do it, it depends on you, but after SharpHound is inside, you can execute it with this command:
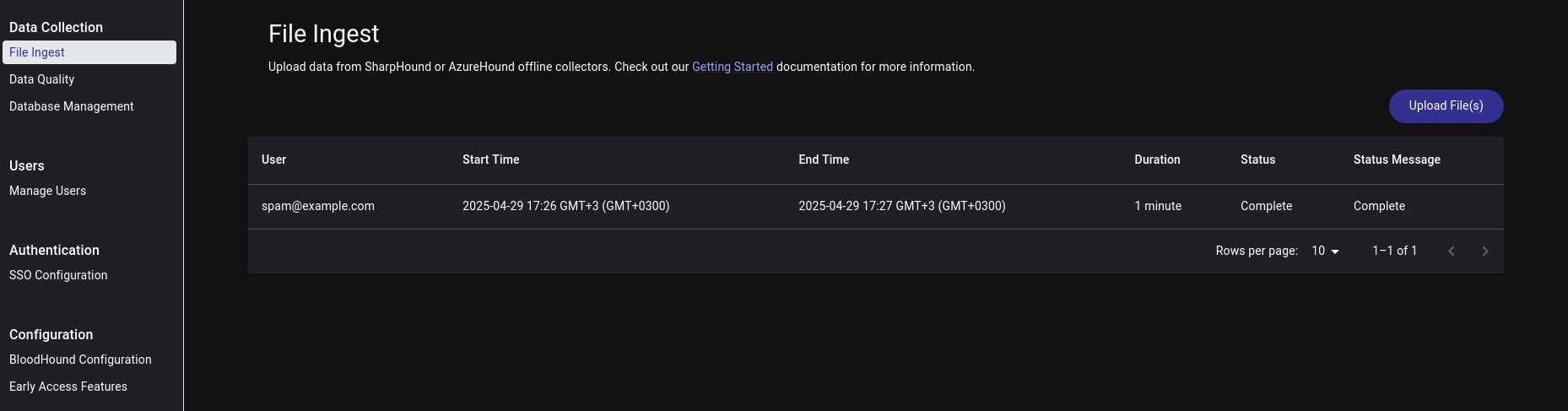
Then wait, and take your zip file back, and put it load it into BloodHound Session in Administration -> Data Collection -> File Ingestion.
If you want to just test tool, you can download example zip file here: [LINK]
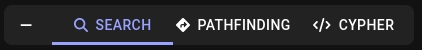
Explore
So basically we have 3 fields: Search, Pathfinding, Cypher:
In Search, we can SEARCH for different objects in AD, like users, ou, gpo, etc. We can specify type with tags like
gpo:user:domain:
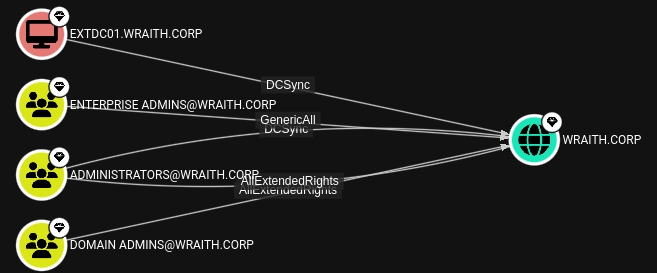
In Pathfinding (my favorite feature by now) you can make a path FROM -> TO objects. As example I will be using domain from my HTB Academy learning where we was needed to find path from wley to adunn:
So here we can see that if there is a chain of connections/accesses, it will automatically make a path.
Also what is awesome, is that each Edge Label has more details and even references for more research and how you could abuse it from Linux or Windows, as example I will use DCSync label:
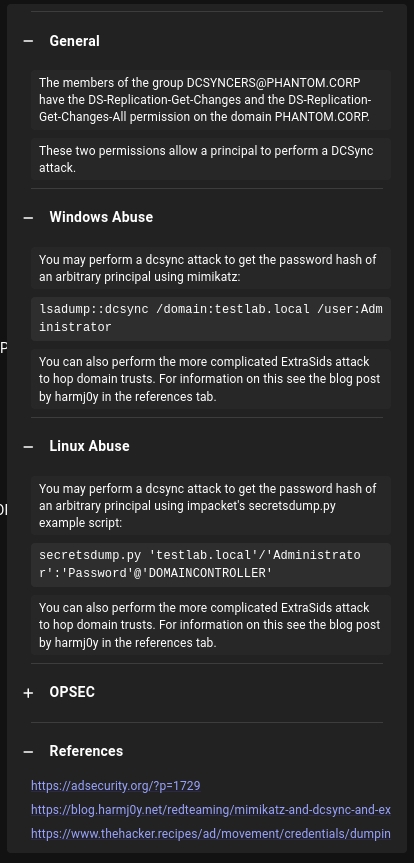
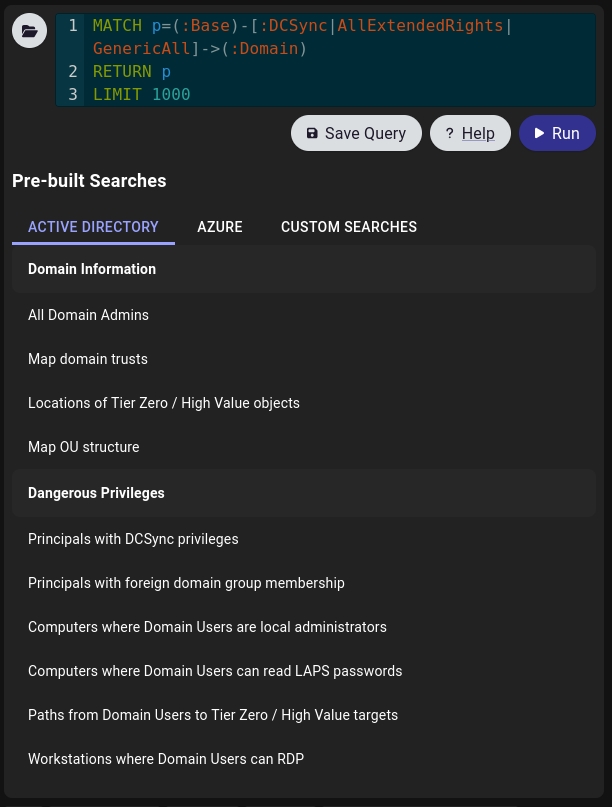
In Cypher we can use custom, or pre-built searches, which can make search for certain info easier.
Group Management
In Group Management section we can check two Groups: Owned (skull logo) and High Value (diamond logo), environment and we can put a filters to check what, and how much of different objects we have, to later check them in Explore
Administration
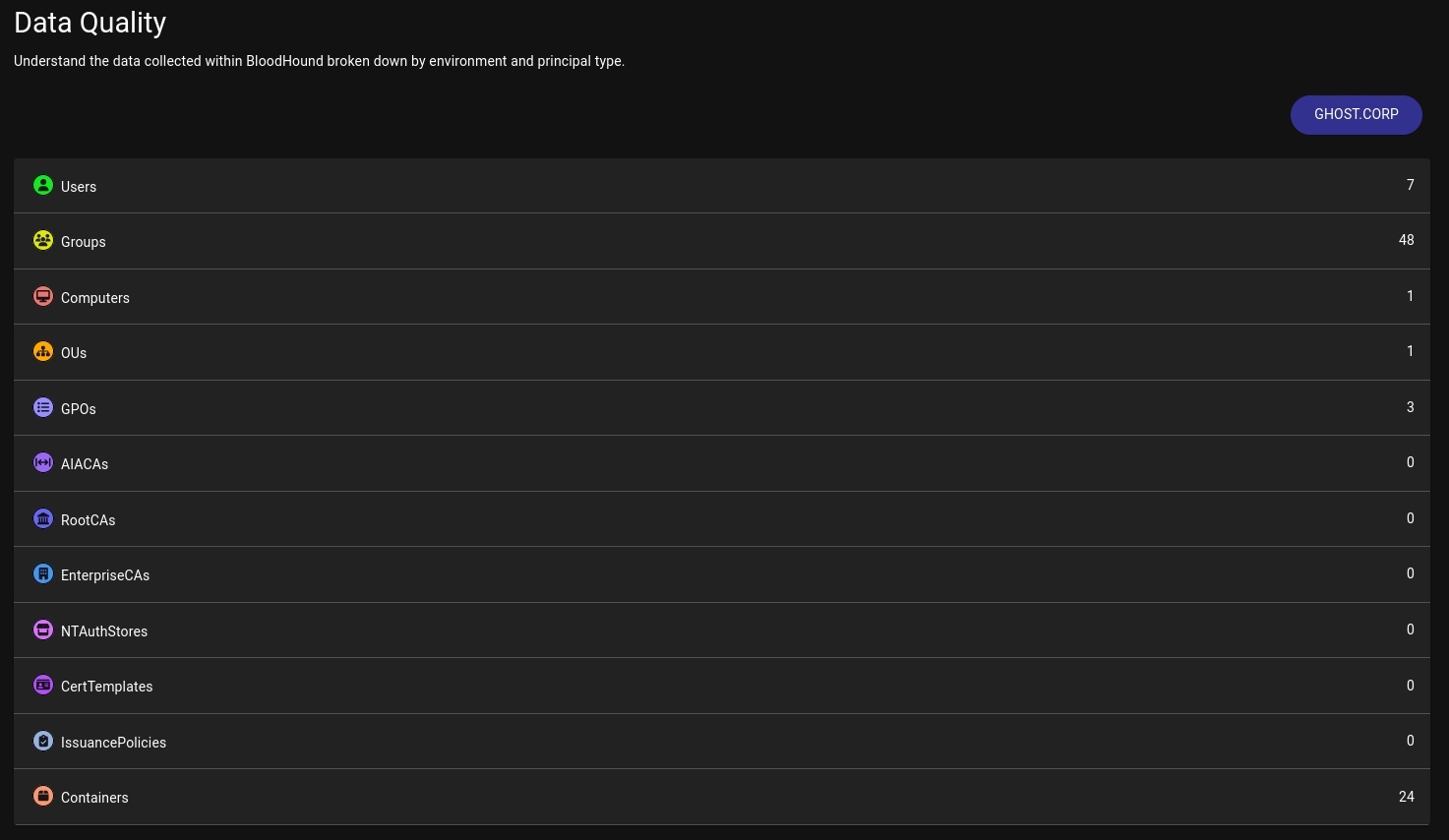
Except Ingest File section (where we uploaded our SharpHound output), we can use Data Quality, where we can see list of objects we have:
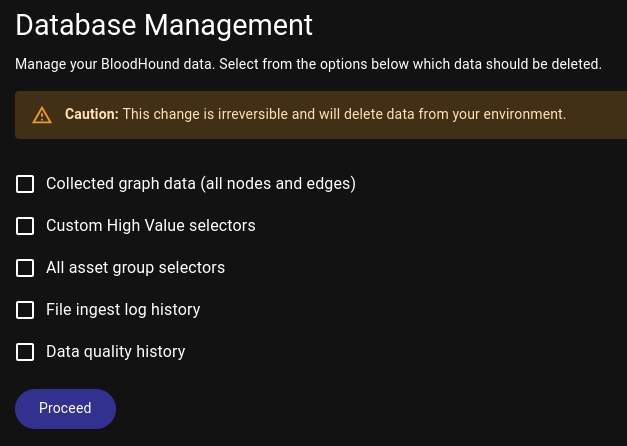
And also we can delete our data (because if we imported data in BH, it's not deleted, even if we are closing the BH session) in Database Management:
INTERFACE
Labels
Yeah, we made a quick run on recon options, but there are also a few options which could customize our schemas, like Hide Labels, where there are two types of labels: Edge and Node Label where Node Label is label of AD Object, and Edge Label describing how nodes are connected with each other. Also with right click you can mark object as Owned (skull mark), if you pwned it.
Layout
It's simple, there are two ways of layout: Standart and Sequential
Layout of nodes isn't fixed, and you can move nodes with mouse as you want.
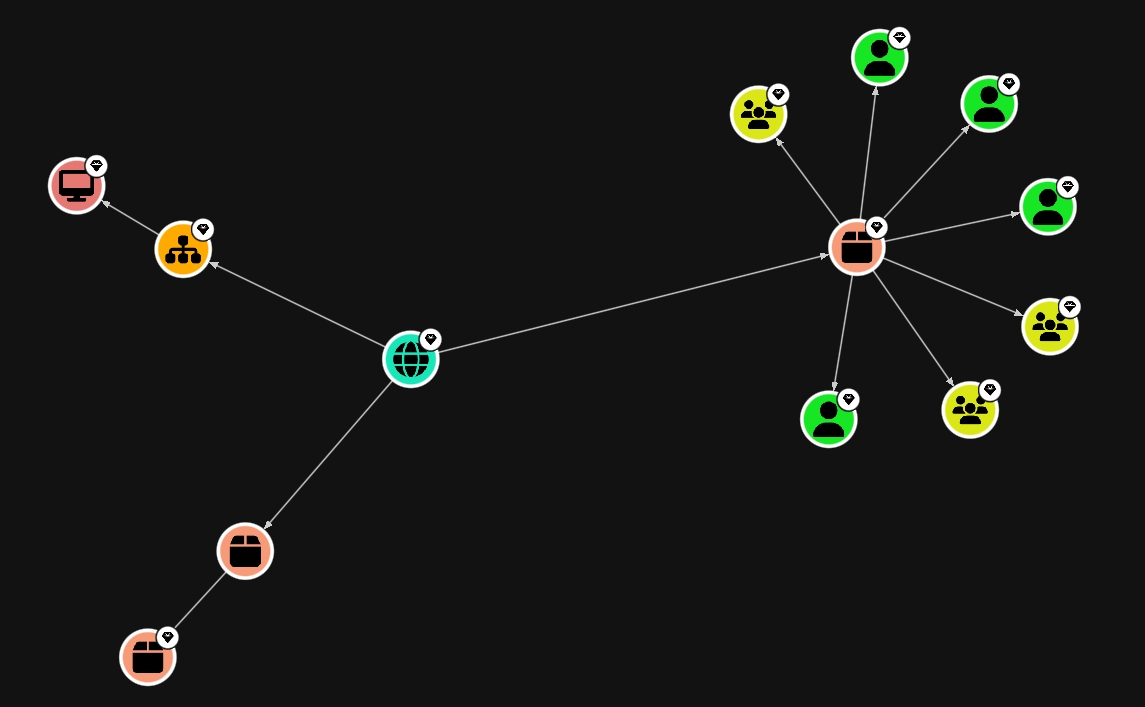
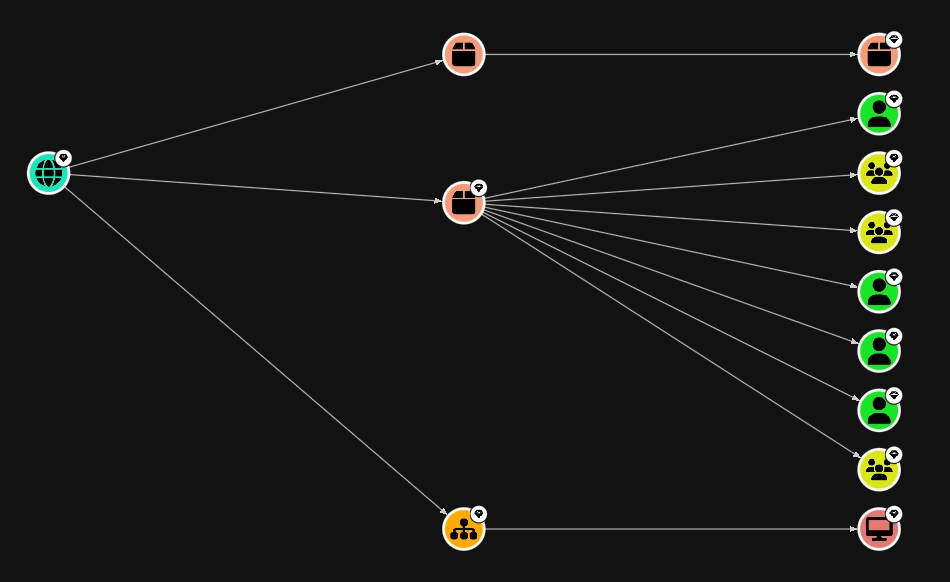
Icons
As you seen, BloodHound has a bunch of icons, and I don't why, but I wanted to make a list of every icon and what it is (also design and color choices are PRETTY)